Risk assessment sets the stage for proactive decision-making, offering a structured approach to identifying, analyzing, and mitigating potential threats. Understanding risk assessment methodologies is crucial for organizations across all sectors, from minimizing financial losses to ensuring operational efficiency and safeguarding against legal repercussions. This guide provides a comprehensive overview of the process, covering key definitions, practical techniques, and essential considerations for effective risk management.
We will explore various methods for evaluating risk, from qualitative assessments to quantitative analysis, examining their strengths and weaknesses. The process of identifying hazards and vulnerabilities will be detailed, with practical examples drawn from different industries. We will delve into strategies for controlling and mitigating identified risks, including risk avoidance, reduction, transfer, and acceptance. Finally, the importance of effective communication and ongoing monitoring will be emphasized, ensuring that risk assessments remain relevant and effective over time.
Defining Risk Assessment
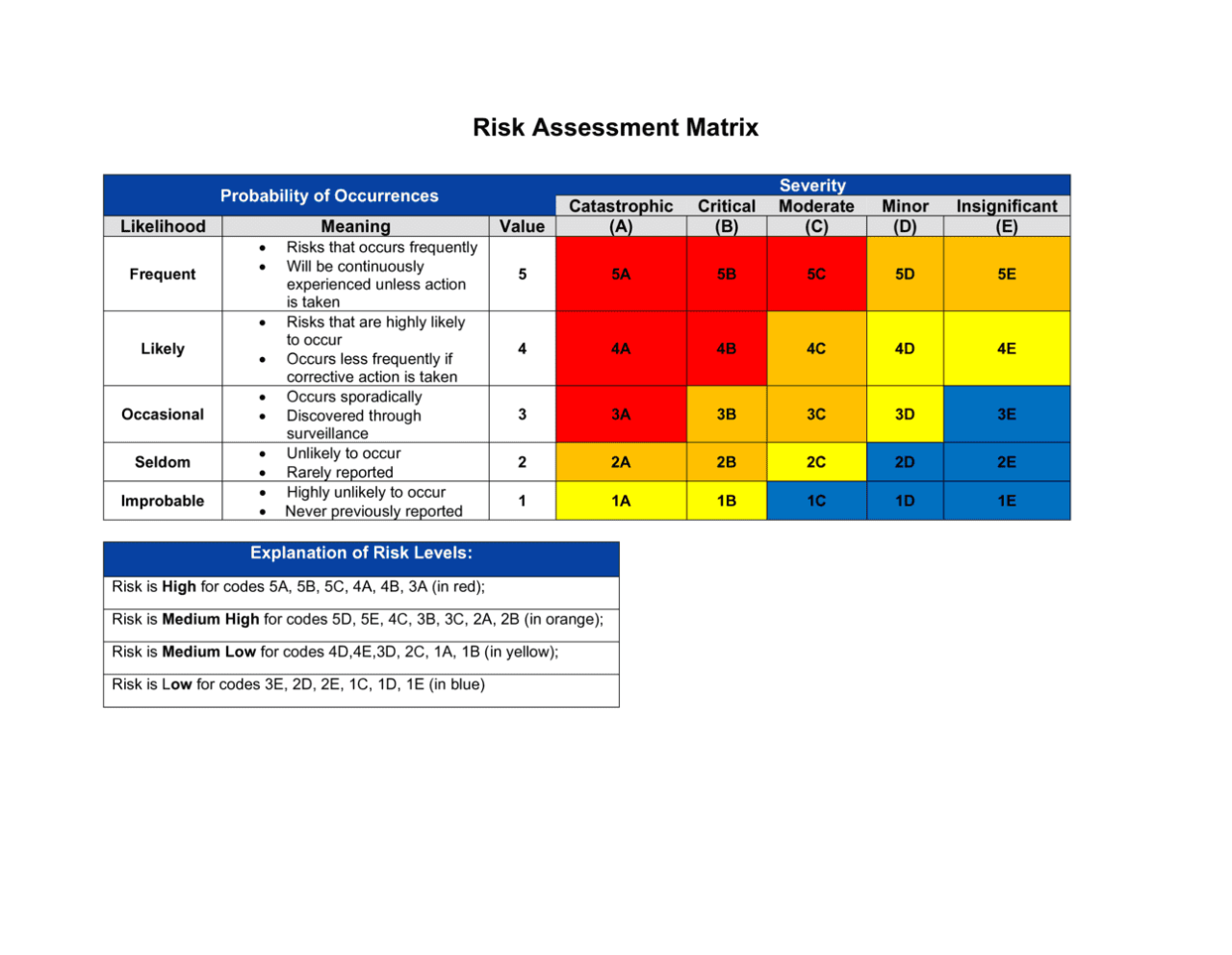
Risk assessment is a systematic process used to identify hazards, analyze potential risks, and determine appropriate control measures. Its purpose is to proactively manage potential negative consequences, ensuring safety, minimizing losses, and improving overall efficiency. The scope of a risk assessment can vary widely depending on the context, ranging from a simple evaluation of a single task to a comprehensive analysis of an entire organization’s operations.
Risk assessment frameworks typically incorporate several key elements. These include defining the scope and objectives of the assessment, identifying potential hazards and vulnerabilities, analyzing the likelihood and severity of potential risks, evaluating existing controls and their effectiveness, and determining appropriate risk mitigation strategies. Effective frameworks also emphasize communication and collaboration amongst stakeholders, regular review and updating of assessments, and documentation of the entire process.
Qualitative and Quantitative Risk Assessment Methods
Qualitative risk assessment methods utilize subjective judgment and descriptive scales to evaluate risks. These methods are often simpler and quicker to implement than quantitative methods, making them suitable for situations where data is limited or time constraints are significant. Examples include using color-coded matrices (e.g., red, amber, green) to represent risk levels or employing descriptive scales such as “low,” “medium,” and “high” to represent likelihood and impact. Qualitative assessments rely heavily on expert opinion and experience.
Quantitative risk assessment methods, conversely, use numerical data and statistical analysis to evaluate risks. These methods provide a more precise and objective measure of risk, allowing for a more informed decision-making process. They typically involve estimating the probability of an event occurring and the potential consequences if it does. Quantitative methods are more complex and require more data, making them more suitable for situations where a higher level of precision is required. Examples include Fault Tree Analysis (FTA) and Event Tree Analysis (ETA).
Risk Assessment Methodologies
The choice of risk assessment methodology depends on the specific context, available resources, and desired level of detail. Several methodologies exist, each with its own strengths and weaknesses.
| Methodology Name | Description | Advantages | Disadvantages |
|---|---|---|---|
| Failure Mode and Effects Analysis (FMEA) | Systematic approach to identify potential failure modes in a system and assess their effects. | Identifies potential failures early in the design process; relatively simple to implement. | Can be time-consuming for complex systems; relies on expert judgment. |
| Fault Tree Analysis (FTA) | Deductive approach that works backward from an undesired event to identify the contributing causes. | Provides a clear visual representation of potential failure pathways; useful for complex systems. | Can be complex and time-consuming; requires detailed knowledge of the system. |
| Hazard and Operability Study (HAZOP) | Systematic review of a process or system to identify potential hazards and operability problems. | Comprehensive approach that considers a wide range of potential hazards; useful for complex processes. | Can be time-consuming and resource-intensive; requires experienced HAZOP leaders. |
| Bowtie Analysis | Combines FTA and Event Tree Analysis to show the cause-and-effect relationships between hazards, controls, and consequences. | Provides a holistic view of risks; useful for identifying and managing risks effectively. | Can be complex and require specialized software; needs experienced analysts. |
Identifying Hazards and Vulnerabilities
Identifying hazards and vulnerabilities is a crucial first step in any effective risk assessment. This process involves systematically examining a given context to pinpoint potential sources of harm and the weaknesses that could expose individuals, assets, or the organization to those harms. A thorough understanding of both hazards and vulnerabilities is necessary for implementing appropriate risk mitigation strategies.
This section details a systematic approach to identifying hazards and vulnerabilities, provides examples across various industries, and highlights the interconnectedness of these two concepts.
Hazard Identification Process
Identifying potential hazards requires a structured approach. This typically involves brainstorming sessions, checklists, hazard and operability studies (HAZOP), and reviewing historical incident data. Each method offers a unique perspective, contributing to a more comprehensive understanding of potential risks. For instance, brainstorming sessions encourage diverse perspectives, while checklists ensure consistency and completeness. HAZOP systematically examines deviations from design intent, and reviewing historical data reveals recurring patterns and vulnerabilities. The ultimate goal is to create a comprehensive inventory of potential hazards within the operational context.
Vulnerability Identification Process
Once hazards are identified, the next step is to determine vulnerabilities. This involves analyzing the weaknesses or gaps in existing safeguards that could allow a hazard to cause harm. This analysis often involves assessing the effectiveness of existing controls, examining the physical environment, reviewing operational procedures, and evaluating human factors such as training and competency. A systematic vulnerability assessment ensures that all potential weaknesses are identified, prioritized, and addressed. For example, a vulnerability assessment might reveal inadequate security measures, poorly designed equipment, or insufficient employee training as weaknesses that could exacerbate the impact of a specific hazard.
Examples of Hazards and Vulnerabilities Across Industries
The following examples illustrate common hazards and vulnerabilities across different sectors. It is important to note that this list is not exhaustive, and the specific hazards and vulnerabilities will vary depending on the specific context and industry.
- Healthcare:
- Hazard: Infectious diseases. Vulnerability: Inadequate infection control protocols, insufficient personal protective equipment (PPE).
- Hazard: Medical errors. Vulnerability: Poor communication between healthcare professionals, inadequate training, lack of standardized procedures.
- Manufacturing:
- Hazard: Machinery malfunction. Vulnerability: Lack of regular maintenance, inadequate safety guards, insufficient employee training on safe operating procedures.
- Hazard: Chemical spills. Vulnerability: Inadequate containment measures, lack of emergency response plan, insufficient personal protective equipment (PPE).
- Information Technology:
- Hazard: Cyberattacks. Vulnerability: Weak passwords, outdated software, lack of firewalls and intrusion detection systems.
- Hazard: Data breaches. Vulnerability: Inadequate data encryption, insufficient access controls, lack of employee awareness of security best practices.
- Finance:
- Hazard: Fraud. Vulnerability: Weak internal controls, lack of independent audits, insufficient employee background checks.
- Hazard: Market volatility. Vulnerability: Inadequate risk management strategies, lack of diversification, insufficient capital reserves.
Analyzing and Evaluating Risks

Analyzing and evaluating identified risks is crucial for effective risk management. This involves determining the likelihood of each risk occurring and the potential impact if it does. This assessment allows for prioritization of risks and the allocation of resources to mitigation strategies. A variety of methods can be employed, each with its strengths and weaknesses.
Risk Likelihood and Impact Assessment Methods
Several methods exist for assessing risk likelihood and impact. Qualitative methods rely on expert judgment and descriptive scales (e.g., low, medium, high), while quantitative methods utilize numerical data and statistical analysis. Qualitative approaches are often simpler and quicker, but less precise, while quantitative methods offer greater precision but require more data and expertise. A common approach involves combining both qualitative and quantitative elements. For example, assigning numerical values to qualitative descriptions (e.g., low=1, medium=2, high=3) allows for a more structured analysis.
Risk Matrices and Their Applications
Risk matrices are visual tools used to represent the likelihood and impact of risks. They typically plot likelihood on one axis and impact on the other, creating a grid with different risk levels represented by color-coding or numerical values. Different matrices may use varying scales and classifications. For example, one matrix might use a 3×3 grid (low, medium, high for both likelihood and impact), while another might use a 5×5 grid with more granular levels. The choice of matrix depends on the context and the level of detail required. A simple 3×3 matrix might suffice for a small project, whereas a more complex matrix might be necessary for a large-scale undertaking with numerous stakeholders. A larger matrix allows for more nuanced risk assessment and prioritization.
Calculating Risk Scores Using a Simple Matrix, Risk assessment
A simple risk matrix can be used to calculate a risk score by multiplying the likelihood score by the impact score. For example, using a 3×3 matrix with likelihood and impact scores ranging from 1 (low) to 3 (high):
Risk Score = Likelihood Score x Impact Score
Consider a risk with a likelihood of “medium” (score of 2) and an impact of “high” (score of 3). The risk score would be 2 x 3 = 6. Risks with higher scores are generally considered higher priority and require more attention. This simple calculation provides a quantifiable measure for comparing and prioritizing risks.
Example of Risk Analysis: Cybersecurity Breach
Let’s consider a scenario of a cybersecurity breach for a small e-commerce business.
| Risk | Likelihood (1-3) | Impact (1-3) | Risk Score |
|---|---|---|---|
| Phishing attack leading to data breach | 2 (Medium) | 3 (High) | 6 |
| Malware infection compromising customer data | 1 (Low) | 3 (High) | 3 |
| Denial-of-service attack disrupting website access | 1 (Low) | 2 (Medium) | 2 |
This simple analysis shows that a phishing attack poses the highest risk (score of 6), requiring immediate attention and mitigation strategies, such as employee training on phishing awareness and robust security protocols. The other risks, while present, are deemed lower priority based on their calculated scores. This allows for resource allocation focused on addressing the most critical vulnerabilities first.
Communicating and Monitoring Risk
Effective communication is the cornerstone of a successful risk management program. Without clear and consistent communication, even the most meticulously crafted risk assessment is rendered ineffective. Stakeholders need to understand the identified risks, the potential consequences, and the mitigation strategies in place. This ensures buy-in, facilitates collaboration, and promotes a culture of safety and preparedness.
Effective communication ensures that all relevant stakeholders are informed about the identified risks and the steps taken to mitigate them. This transparency builds trust and confidence, and fosters a collaborative environment where everyone works together to reduce risks. Furthermore, clear communication helps to manage expectations and avoid misunderstandings that could exacerbate the impact of a risk event.
Risk Communication Plan
A well-defined communication plan is crucial for disseminating risk assessment findings effectively. This plan should Artikel the target audience (e.g., senior management, employees, customers, regulators), the communication channels to be used (e.g., reports, presentations, emails, meetings), the frequency of communication, and the key messages to be conveyed. The plan should also specify who is responsible for communicating the information and how feedback will be collected and addressed. For instance, a company might use regular safety meetings for employees, formal reports for senior management, and public announcements for customers, tailoring the message and medium to the audience’s needs and understanding.
Visual Representations of Risk Information
Visual representations are powerful tools for communicating complex risk information in a clear and concise manner. They can significantly improve understanding and engagement with the assessment findings.
Example 1: Heat Map
A heat map uses a color gradient to represent the level of risk associated with different factors or areas. For example, a heat map could show the risk level of different processes within a company, with red representing high risk, yellow representing medium risk, and green representing low risk. The color intensity could correspond to the severity of the potential consequences. This provides a quick and intuitive overview of the overall risk profile.
Example 2: Bar Chart
A bar chart can be used to compare the relative risk levels of different hazards or vulnerabilities. The height of each bar could represent the likelihood or impact of a specific risk. A simple color scheme, such as using different shades of blue for different risk levels, would enhance readability. This allows for easy comparison and prioritization of risks.
Example 3: Risk Matrix
A risk matrix is a visual tool that plots risks based on their likelihood and impact. It uses a two-dimensional grid where the x-axis represents likelihood and the y-axis represents impact. Each risk is plotted on the matrix, allowing for a quick assessment of its overall severity. Different colors or symbols can be used to categorize risks into different levels of severity, with a clear legend explaining the color-coding. For example, a risk with high likelihood and high impact would be plotted in the top-right corner and highlighted in red, indicating a critical risk requiring immediate attention. This visual representation aids in prioritizing risk mitigation efforts.
Monitoring and Reviewing Risk Assessments
Risk assessments are not static documents; they require ongoing monitoring and review to ensure they remain relevant and accurate. Changes in the business environment, new technologies, regulatory requirements, and incident reports all necessitate updates to the assessment. A regular review schedule (e.g., annually or after significant changes) should be established. This process involves comparing the current risk profile with the previous assessment, identifying any changes in risk levels, and updating the mitigation strategies accordingly. Documentation of these reviews is essential for maintaining a comprehensive risk management record and demonstrating due diligence. For example, a manufacturing plant might update its risk assessment after a new piece of equipment is installed, or after a near-miss incident highlights a previously unidentified vulnerability. The process involves reassessing the likelihood and impact of the relevant risks, and adjusting mitigation plans as needed.
Legal and Regulatory Considerations: Risk Assessment

Legal and regulatory compliance is paramount in conducting effective risk assessments. Failure to adhere to these frameworks can lead to significant repercussions, impacting an organization’s reputation, financial stability, and even its legal standing. This section will explore the legal and regulatory landscape surrounding risk assessment within the healthcare industry, focusing on patient safety and data privacy.
The healthcare industry operates under a complex web of regulations designed to protect patient safety and privacy. These regulations significantly influence the design and implementation of risk assessment processes, demanding a rigorous and documented approach. Non-compliance can result in substantial fines, legal action, and damage to public trust.
Relevant Legal and Regulatory Requirements in Healthcare
Numerous laws and regulations govern risk assessment in healthcare. Key examples in the United States include the Health Insurance Portability and Accountability Act (HIPAA), which mandates the protection of patient health information (PHI), and the Joint Commission standards, which establish accreditation requirements encompassing risk management practices. These regulations dictate specific procedures for identifying, analyzing, and mitigating risks related to patient safety, data security, and infection control. For instance, HIPAA requires covered entities to implement administrative, physical, and technical safeguards to protect PHI. The Joint Commission’s standards require healthcare organizations to conduct regular risk assessments to identify potential hazards and implement corrective actions. Failure to comply with these regulations can lead to severe penalties, including hefty fines and the loss of accreditation.
Consequences of Inadequate Risk Assessments in Healthcare
Inadequate risk assessments in healthcare can have severe consequences. Failing to identify and mitigate risks related to patient safety can lead to medical errors, adverse events, and even patient death. Similarly, neglecting data security risks can result in data breaches, exposing sensitive patient information and leading to significant financial losses and reputational damage. In the context of infection control, inadequate risk assessments can contribute to outbreaks of healthcare-associated infections (HAIs), resulting in increased morbidity, mortality, and healthcare costs. These consequences can lead to legal liabilities, including lawsuits from patients or their families, and regulatory sanctions from agencies like the Centers for Medicare & Medicaid Services (CMS). For example, a hospital failing to adequately assess and mitigate the risk of a medication error leading to patient harm could face substantial legal action and reputational damage.
Influence of Legal and Regulatory Frameworks on Risk Assessment Processes
Legal and regulatory frameworks significantly influence the design and implementation of risk assessment processes in healthcare. Regulations often dictate the methodology, documentation requirements, and frequency of risk assessments. They also specify the types of risks that must be addressed, such as those related to patient safety, infection control, and data security. Compliance with these frameworks necessitates the development of robust risk assessment procedures, including clear protocols for identifying hazards, analyzing risks, and implementing control measures. Regular audits and reviews are also essential to ensure ongoing compliance and effectiveness. The implementation of a risk management system aligned with legal and regulatory requirements demonstrates a commitment to patient safety and responsible healthcare practices. This, in turn, helps build trust with patients, regulators, and the wider community.
Ending Remarks
Effective risk assessment is not a one-time event but an ongoing process that requires continuous monitoring and adaptation. By implementing the strategies and methodologies Artikeld in this guide, organizations can proactively manage risk, improve operational efficiency, and protect their valuable assets. Understanding the legal and regulatory landscape is equally crucial to ensure compliance and minimize potential liabilities. A robust risk assessment framework empowers organizations to make informed decisions, minimize disruptions, and ultimately achieve sustainable success.
FAQ Guide
What is the difference between a hazard and a risk?
A hazard is a potential source of harm, while a risk is the likelihood and potential impact of that harm occurring.
How often should risk assessments be reviewed?
The frequency of review depends on the context, but regular updates (e.g., annually or after significant changes) are recommended.
Who should be involved in a risk assessment?
A multidisciplinary team with expertise relevant to the assessed area is ideal. This may include management, staff, and external consultants.
What are the potential consequences of inadequate risk assessment?
Consequences can range from financial losses and reputational damage to legal penalties and even safety incidents.